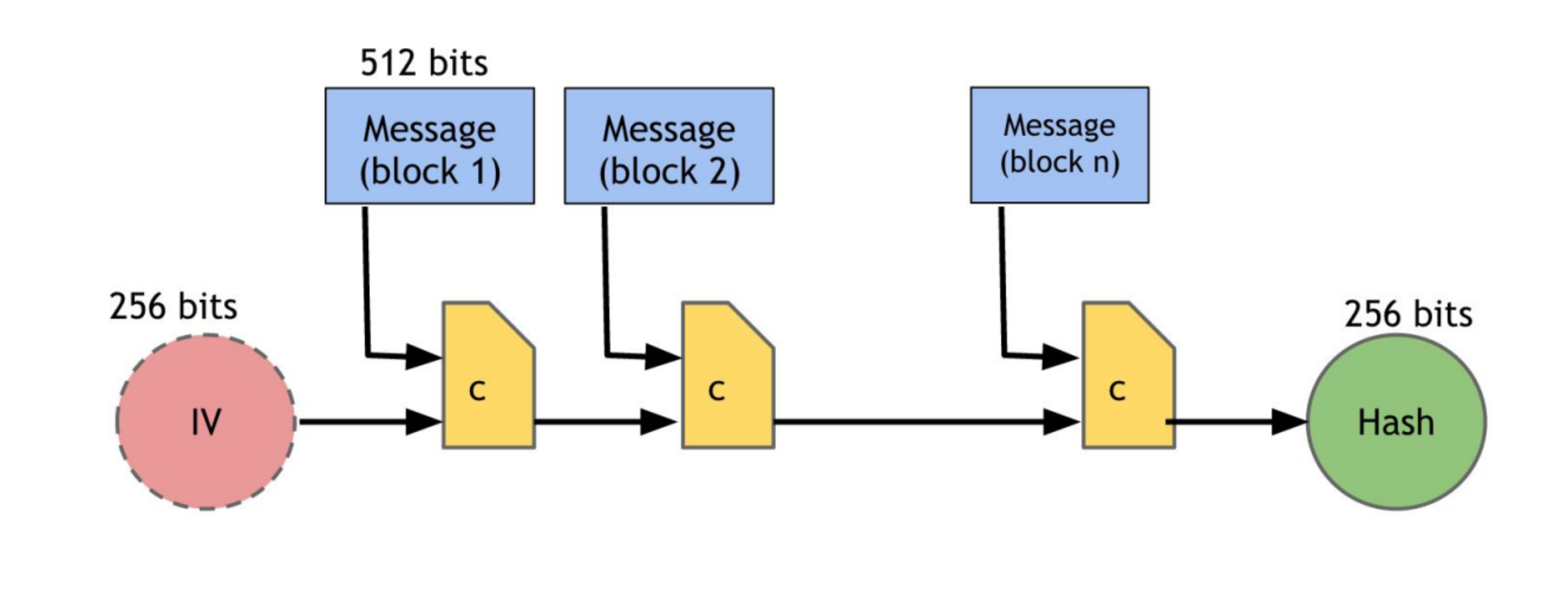
SHA-256: Building the Hash Algorithm from Scratch
Step-by-step journey of building the SHA-256 hash algorithm from the ground up

Step-by-step journey of building the SHA-256 hash algorithm from the ground up
](https://www.tony.software/papers/bitcoin_whitepaper.jpg)
A purely peer-to-peer version of electronic cash would allow online payments to be sent directly from one party to another without going through a financial institution. Digital signatures provide part of the solution, but the main benefits are lost if a trusted third party is still required to prevent double-spending. We propose a solution to the double-spending problem using a peer-to-peer network. The network timestamps transactions by hashing them into an ongoing chain of hash-based proof-of-work, forming a record that cannot be changed without redoing the proof-of-work. The longest chain not only serves as proof of the sequence of events witnessed, but proof that it came from the largest pool of CPU power. As long as a majority of CPU power is controlled by nodes that are not cooperating to attack the network, they’ll generate the longest chain and outpace attackers. The network itself requires minimal structure. Messages are broadcast on a best effort basis, and nodes can leave and rejoin the network at will, accepting the longest proof-of-work chain as proof of what happened while they were gone. ...
](https://www.tony.software/books/build_your_own_blockchain.webp)
Build Your Own Blockchain book provides a comprehensive introduction to blockchain and distributed ledger technology. Intended as an applied guide for hands-on practitioners, the book includes detailed examples and in-depth explanations of how to build and run a blockchain from scratch. Through its conceptual background and hands-on exercises, this book allows students, teachers and crypto enthusiasts to launch their first blockchain while assuming prior knowledge of the underlying technology. How do I build a blockchain? How do I mint a cryptocurrency? How do I write a smart contract? How do I launch an initial coin offering (ICO)? These are some of questions this book answers. Starting by outlining the beginnings and development of early cryptocurrencies, it provides the conceptual foundations required to engineer secure software that interacts with both public and private ledgers. The topics covered include consensus algorithms, mining and decentralization, and many more. ...
](https://www.tony.software/papers/fips_pub_180_4.jpg)
The standard specifies hash algorithms that can be used to generate digests of messages. The digests are used to detect whether messages have been changed since the digests were generated.