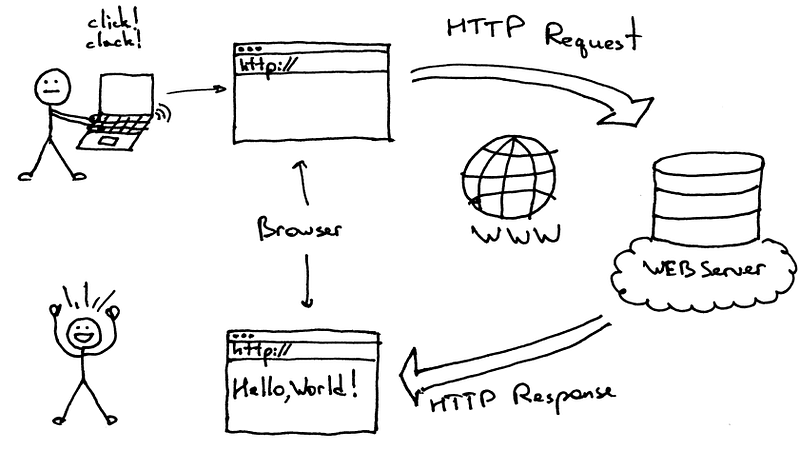
Introduction
Recent research shows that in the second quarter of 2022, the average time spent on the Internet per person was 397 minutes (6 hours and 37 minutes) per day [1]. Most of the traffic generated by the average person is transmitted by HTTP, which forms what is known as the World Wide Web, commonly referred as the Web. The Web, allows data objects such as web pages to be available to the network through web servers and can be accessed by client programs such as web browsers. But have you ever wandered what actually happens when you send a request to download a web page from your browser?
If you are interested in learning more about computer networking in depth, I highly recommend checking out Computer Networking: A Top-Down Approach by James Kurose and Keith Ross [2], from which this post is based on!
Morning
Imagine a student named Diego who connects his laptop to the school’s Ethernet
switch and proceeds to download a web page, such as the homepage of this site,
tony.software.
When Diego initially connects his laptop to the network, he is unable to perform any actions, such as downloading a web page, without an IP address. Therefore, the first step taken by Diego’s laptop in relation to the network is to execute the DHCP protocol, which enables it to acquire an IP address from the local DHCP server.
Diego’s laptop generates a DHCP request message and encapsulates it within a
UDP segment. Subsequently, the UDP segment is encapsulated within an IP datagram,
where the destination IP address is set to a broadcast address (255.255.255.255),
and the source IP address is set to 0.0.0.0 since Diego’s laptop doesn’t possess
an IP address yet.
The IP datagram containing the DHCP request message is then encapsulated within
an Ethernet frame. The Ethernet frame is assigned a destination MAC address of
FF:FF:FF:FF:FF:FF to ensure that the frame is broadcasted to all devices connected
to the switch, including the DHCP server if present.
Upon receiving the broadcasted Ethernet frame containing the DHCP request, the router extracts the IP datagram from the Ethernet frame. As the IP datagram’s destination address indicates that it should be processed by upper layer protocols on the current node, the datagram’s payload (a UDP segment) is demultiplexed up to the UDP layer, and the DHCP request message is extracted from the UDP segment. The DHCP server now possesses the DHCP request message.
The DHCP server generates a DHCP ACK message that includes the IP address, the IP address of the DNS server, and the IP address of the default gateway router. This DHCP message is then encapsulated within a UDP segment, which is further encapsulated within an IP datagram, and finally encapsulated within an Ethernet frame.
Diego’s laptop receives the Ethernet frame containing the DHCP ACK, extracts the IP datagram from the Ethernet frame, further extracts the UDP segment from the IP datagram, and finally extracts the DHCP ACK message from the UDP segment. Diego’s DHCP client records the assigned IP address, the IP address of the DNS server, and the IP address of the default gateway router.
Afternoon
In order for the web browser to display the home page of tony.software,
it needs to obtain the IP address of the web server. This translation of
names to IP addresses is facilitated by the DNS protocol. Diego’s laptop
initiates this process by creating a DNS query message, where the domain
tony.software is placed in the question section of the DNS message.
This DNS message is then encapsulated within a UDP segment, which is further
encapsulated within an IP datagram, with the IP destination address being the
DNS server obtained from the DHCP ACK message.
Diego’s laptop proceeds to encapsulate the datagram containing the DNS query message within an Ethernet frame. This frame will be directed to the gateway router within Diego’s school network at the link layer. However, although Diego’s laptop knows the IP address of the school’s gateway router through the DHCP ACK message, it is unaware of the router’s MAC address. To acquire the MAC address of the gateway router, Diego’s laptop employs the ARP protocol.
Diego’s laptop generates an ARP query message, with the target IP address set
to the default gateway’s IP address. The ARP message is then encapsulated within
an Ethernet frame, utilizing a broadcast destination address (FF:FF:FF:FF:FF:FF),
and the Ethernet frame is sent to the switch, which distributes the frame to all
connected devices, including the gateway router.
The gateway router receives the frame containing the ARP query message on its interface connected to the school network. Upon finding that the target IP address in the ARP message matches the IP address of its interface, the gateway router prepares an ARP reply that includes its MAC address. Diego’s laptop receives the frame containing the ARP reply message and extracts the MAC address of the gateway router from the reply.
Finally, Diego’s laptop is now equipped to address the Ethernet frame containing the DNS query to the MAC address of the gateway router. It’s important to note that the IP datagram within this frame possesses an IP destination address of the DNS server, while the frame itself has a destination MAC address of the gateway router. Diego’s laptop sends this frame to the switch, which in turn delivers the frame to the gateway router.
Evening
The gateway router receives the frame and extracts the IP datagram that holds the DNS query. By referring to its forwarding table, the router determines that the datagram should be forwarded to the router in the Comcast network.
Upon receiving the frame, the router in the Comcast network extracts the IP datagram and examines the destination address. Using its forwarding table, which is populated by Comcast’s intra-domain protocols like RIP or OSPF, as well as the Internet’s inter-domain protocol BGP, it identifies the appropriate outgoing interface to forward the datagram towards the DNS server.
Eventually, the IP datagram carrying the DNS query reaches the DNS server.
The DNS server extracts the DNS query message and performs a lookup in its
DNS database for the name tony.software. If the corresponding DNS resource
record containing the IP address for tony.software is present in the server’s
cache, the DNS server retrieves it. The DNS server constructs a DNS reply message
that includes the mapping of hostname to IP address and places this reply message
within a UDP segment. Subsequently, the segment is encapsulated within an IP
datagram addressed to Diego’s laptop.
Diego’s laptop extracts the IP address of the tony.software server from the
DNS message. Finally, after a series of operations, Diego’s laptop is now prepared
to establish communication with the tony.software server!
Night
Now that Diego’s laptop has obtained the IP address of tony.software, it can
establish a TCP socket to transmit the HTTP GET message to tony.software. Firstly,
Diego’s laptop generates a TCP SYN segment, encapsulates it within an IP datagram
with the destination IP address set to tony.software, and then places the
datagram within a frame with the gateway router’s MAC address as the destination.
Subsequently, the frame is sent to the switch.
Eventually, the datagram containing the TCP SYN reaches tony.software.
The TCP SYN message is extracted from the datagram and demultiplexed to the welcome
socket. A connection socket is created to establish the TCP connection between
the tony.software HTTP server and Diego’s laptop. Subsequently, a TCP SYNACK
segment is generated, placed within a datagram addressed to Diego’s laptop,
and then encapsulated within a link-layer frame suitable for the link connecting
tony.software its first-hop router.
With the socket on Diego’s laptop now prepared to send data to tony.software,
Diego’s browser constructs the HTTP GET message that contains the URL of the
desired resource. The HTTP GET message is written into the socket, where it
becomes the payload of a TCP segment. The TCP segment is placed within a datagram
and sent to the web (HTTP) server.
The web server receives the HTTP GET message from the TCP socket, creates an HTTP response message, incorporates the requested web page content into the body of the response message, and sends the message back through the TCP socket.
The datagram carrying the HTTP reply message is routed through the Tony, Comcast, and school networks, finally reaching Diego’s laptop. Diego’s web browser program reads the HTTP response from the socket, extracts the HTML content for the web page from the body of the response, and ultimately displays the web page! 🚀
As detailed as the above example might seem, we’ve omitted a number of possible additional details and protocols (e.g., NAT running in the school’s gateway router, wireless access to the school’s network, security protocols for encrypting segments or datagrams), and considerations (Web caching, the DNS hierarchy) that one would encounter in the public Internet!
References
- Lin, Y. (n.d.). HOW MUCH TIME DOES THE AVERAGE PERSON SPEND ON THE INTERNET? Oberlo. https://www.oberlo.com/statistics/how-much-time-does-the-average-person-spend-on-the-internet
- Kurose, J., & Ross, K. W. (2012). Computer Networking: A Top-Down Approach (6th Edition). In Addison-Wesley Longman Publishing Co., Inc. eBooks. https://dl.acm.org/citation.cfm?id=2584507